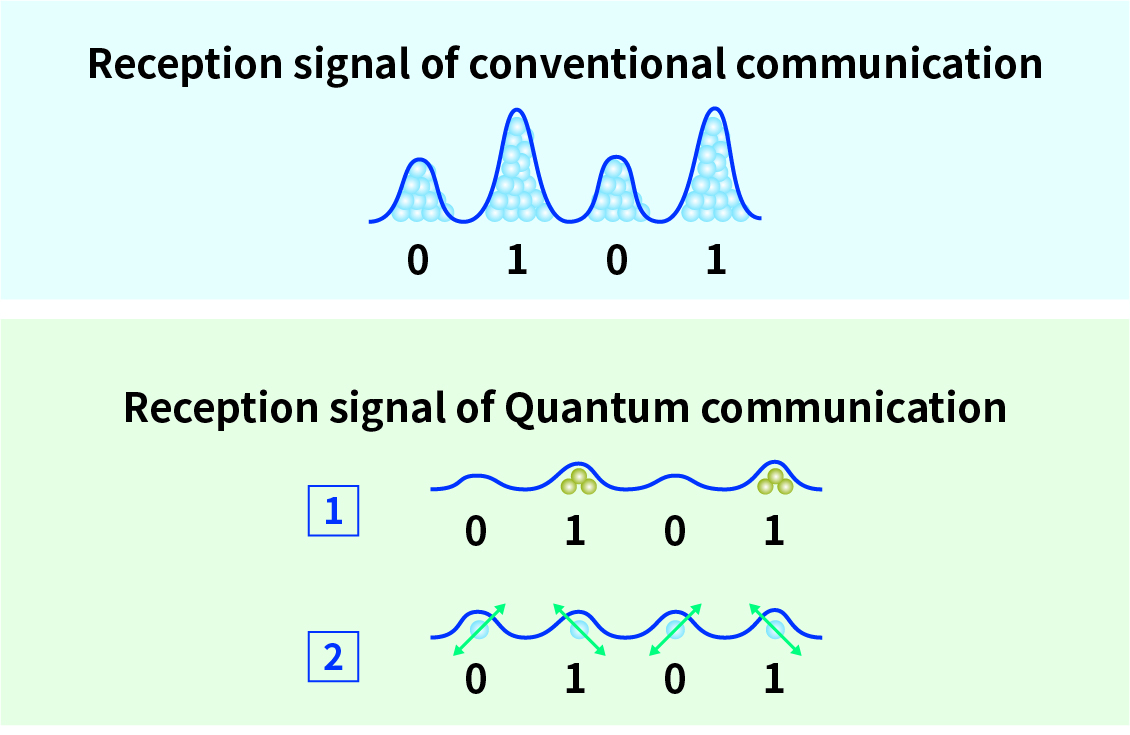
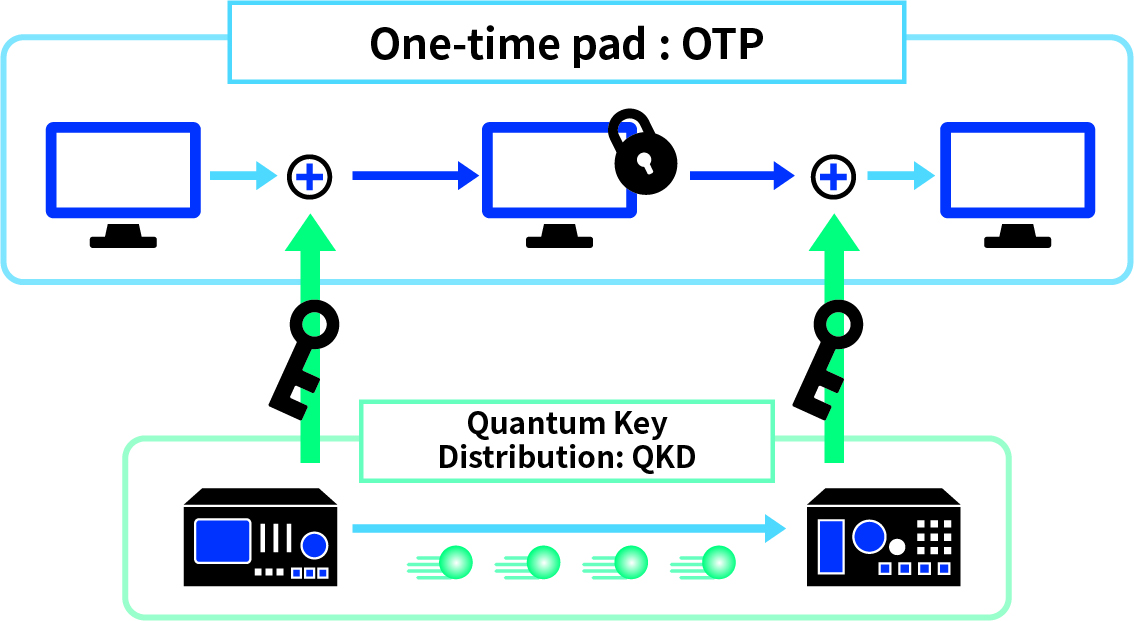
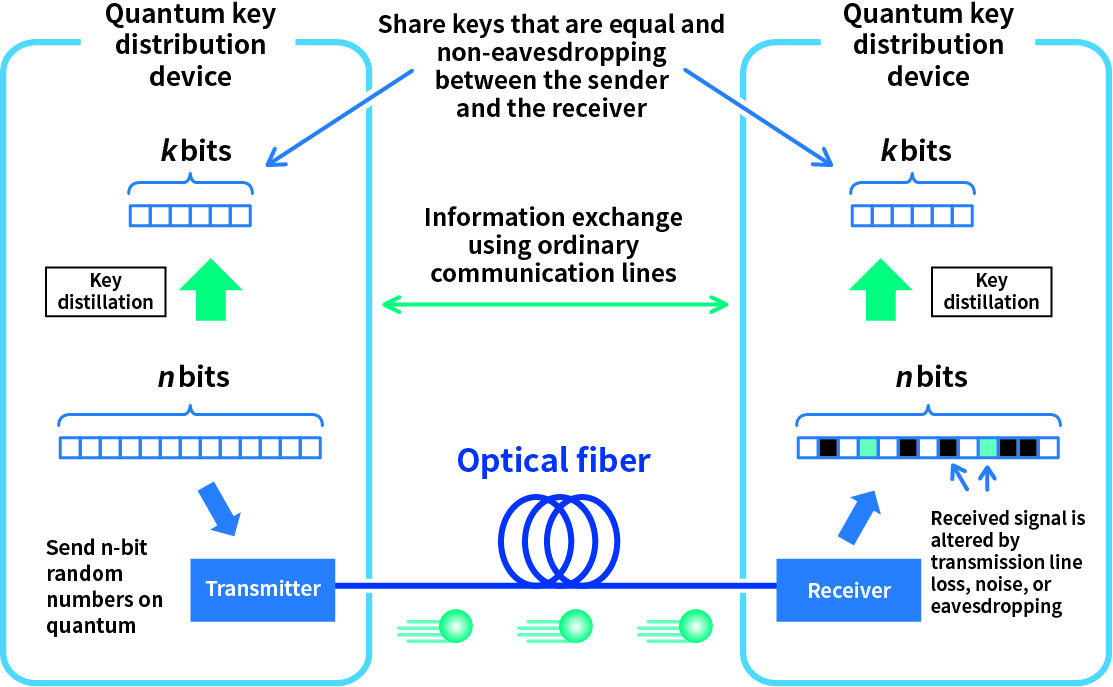
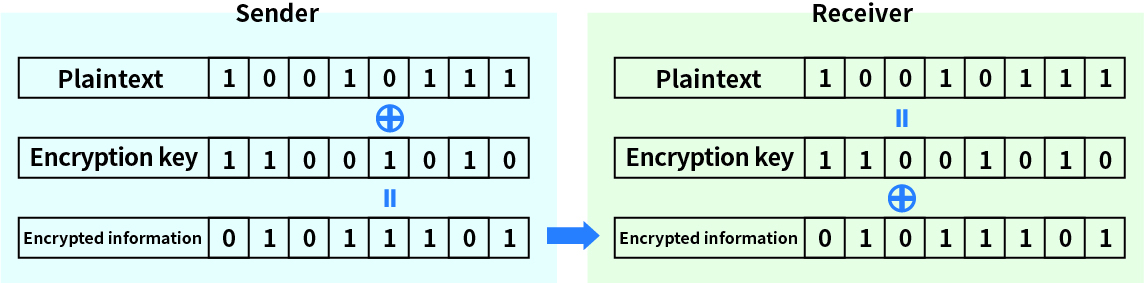
Quantum communication is a technology that applies quantum mechanics to communication. When transmit digital data in conventional communications, 0 and 1 are expressed using electricity or light as signals. However, in quantum communication, 0 and 1 are expressed as signals based on the state of the quantum of light itself (the smallest particle that cannot be further divided). Digital data can be shared between two parties when the sender generates a quantum signal and sends it to the other party, and the receiver measures the signal.
There are two main types of quantum communication. The first is a highly sensitive photodetector that allows the receiver to measure signals that have become weak during communication, enabling ultra-long distance, high-capacity communication. The second is a method in which a receiver measures a signal transmitted by a sender using a single quantum state as a signal, and a method for safely sharing digital data between two parties is devised by making use of the nature of quantum mechanics by setting the signal to the quantum level.